Part II: Information Systems for Strategic Advantage
Chapter 9: The People in Information Systems
Learning Objectives
Upon successful completion of this chapter, you will be able to:
- describe each of the different roles that people play in the design, development, and use of information systems;
- understand the different career paths available to those who work with information systems;
- explain the importance of where the information-systems function is placed in an organization; and
- describe the different types of users of information systems.
Introduction
The opening chapters of this text focused on the technology behind information systems, namely hardware, software, data, and networking. The last chapter covered business processes and the key role they can play in the success of a business. This chapter discusses people, the last component of an information system.
People are involved in information systems in just about every way. People imagine information systems, people develop information systems, people support information systems, and, perhaps most importantly, people use information systems.
The Creators of Information Systems
The first group of people to be considered play a role in designing, developing, and building information systems. These people are generally technical and have a background in programming, analysis, information security, or database design. Just about everyone who works in the creation of information systems has a minimum of a bachelor’s degree in computer science or information systems, though that is not necessarily a requirement. The process of creating information systems will be covered in more detail in Chapter 10.
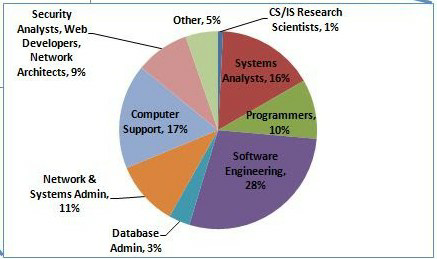
The following chart shows the U. S. Bureau of Labor Statistics projections for computing career employment in 2020.
Systems Analyst
The systems analyst straddles the divide between identifying business needs and imagining a new or redesigned system to fulfill those needs. This individual works with a team or department seeking to identify business requirements and analyze the specific details of an existing system or a system that needs to be built. Generally, the analyst is required to have a good understanding of the business itself, the purpose of the business, the business processes involved, and the ability to document them well. The analyst identifies the different stakeholders in the system and works to involve the appropriate individuals in the analysis process.
Prior to analyzing the problem or the system of concern, the analyst needs to a) clearly identify the problem, b) gain approval for the project, c) identify the stakeholders, and d) develop a plan to monitor the project. The analysis phase of the project can be broken down into five steps.
- Seek out and identify the details
- Specify requirements
- Decide which requirements are most important
- Create a dialog showing how the user interacts with the existing system
- Ask users to critique the list of requirements that have been developed
The analysis phase involves both the systems analyst and the users. It is important to realize the role the users take in the analysis of the system. Users can have significant insights into how well the current system functions as well as suggest improvements.
Once the requirements are determined, the analyst begins the process of translating these requirements into an information systems design. It is important to understand which different technological solutions will work and provide several alternatives to the client, based on the company’s budgetary constraints, technology constraints, and culture. Once the solution is selected, the analyst will create a detailed document describing the new system. This new document will require that the analyst understand how to speak in the technical language of systems developers.
The design phase results in the components of the new system being identified, including how they relate to one another. The designer needs to communicate clearly with software developers as well database administrators by using terminology that is consistent with both of these specialties. The design phase of the project can be broken down into six steps.
- Design the hardware environment
- Design the software
- Design how the new system will interface with the users
- Design hardware interfaces
- Design database tables
- Design system security
A systems analyst generally is not the one who does the actual development of the information system. The design document created by the systems analyst provides the detail needed to create the system and is handed off to a developer to actually write the software and to the database administrator to build the database and tables that will be in the database.
Sometimes the system may be assembled from off-the-shelf components by a person called a systems integrator. This is a specific type of systems analyst that understands how to get different software packages to work with each other.
To become a systems analyst, you should have a background both in the business analysis and in systems design. Many analysts first work as developers and have business experience before becoming system analysts. It is vital for analysts to clearly understand the purpose of the business of interest, realizing that all businesses are unique.
Programmer/Developer
Programmers spend their time writing computer code in a programming language. In the case of systems development, programmers generally attempt to fulfill the design specifications given to them by a systems analyst/designer. Many different styles of software development exist A programmer may work alone for long stretches of time or work as part of a team with other developers. A programmer needs to be able to understand complex processes and also the intricacies of one or more programming languages.
Computer Engineer
Computer engineers design the computing devices that are used every day. There are many types of computer engineers who work on a variety of different types of devices and systems. Some of the more prominent computer engineering jobs are as follows:
- Hardware engineer. A hardware engineer designs hardware and test components such as microprocessors, memory devices, routers, and networks. Many times, a hardware engineer is at the cutting edge of computing technology, creating something brand new. Other times, the hardware engineer’s job is to re-engineer an existing component to work faster or use less power. Many times a hardware engineer’s job is to write code to create a program that will be implemented directly on a computer chip.
- Software engineer. Software engineers tend to focus on a specific area of software such as operating systems, networks, applications, or databases. Software engineers use three primary skill areas: computer science, engineering, and mathematics.
- Systems engineer. A systems engineer takes the components designed by other engineers and makes them all work together, focusing on the integration of hardware and software. For example, to build a computer the mother board, processor, memory, and hard disk all have to work together. A systems engineer has experience with many different types of hardware and software and knows how to integrate them to create new functionality.
- Network engineer. A network engineer understands the networking requirements of an organization and then designs a communications system to meet those needs, using the networking hardware and software, sometimes referred to as a network operating system. Network engineers design both local area networks as well as wide area networks.
There are many different types of computer engineers, and often the job descriptions overlap. While many may call themselves engineers based on a company job title, there is also a professional designation of “professional engineer” which has specific requirements. In the United States each state has its own set of requirements for the use of this title, as do different countries around the world. Most often, it involves a professional licensing exam.
Information Systems Operations and Administration
Another group of information systems professionals are involved in the day-to-day operations and administration of IT. These people must keep the systems running and up-to-date so that the rest of the organization can make the most effective use of these resources.
Computer Operator
A computer operator is the person who oversees the mainframe computers and data centers in organizations. Some of their duties include keeping the operating systems up to date, ensuring available memory and disk storage, providing for redundancy (think electricity, connectivity to the Internet, and database backups), and overseeing the physical environment of the computer. Since mainframe computers increasingly have been replaced with servers, storage management systems, and other platforms, computer operators’ jobs have grown broader and include working with these specialized systems.
Database Administrator
A Database Administrator (DBA) is the person who designs and manages the databases for an organization. This person creates and maintains databases that are used as part of applications or the data warehouse. The DBA also consults with systems analysts and programmers on projects that require access to or the creation of databases.
Help Desk/Support Analyst
Most mid-size to large organizations have their own information technology help desk. The help desk is the first line of support for computer users in the company. Computer users who are having problems or need information can contact the help desk for assistance. Many times a help desk worker is a junior level employee who is able to answer basic issues that users need assistance with. Help desk analysts work with senior level support analysts or have a computer knowledgebase at their disposal to help them investigate the problem at hand. The help desk is a great place to break into working in IT because it exposes you to all of the different technologies within the company. A successful help desk analyst should have good communications skills and a sincere interest in helping users.
Trainer
A computer trainer conducts classes to teach people specific computer skills. For example, if a new ERP system is being installed in an organization, one part of the implementation process is to teach all of the users how to use the new system. A trainer may work for a software company and be contracted to come in to conduct classes when needed; a trainer may work for a company that offers regular training sessions. Or a trainer may be employed full time for an organization to handle all of their computer instruction needs. To be successful as a trainer you need to be able to communicate technical concepts clearly and demonstrate patience with learners.
Managing Information Systems
The management of information-systems functions is critical to the success of information systems within the organization. Here are some of the jobs associated with the management of information systems.
CIO
The Chief Information Officer (CIO) is the head of the information-systems function. This person aligns the plans and operations of the information systems with the strategic goals of the organization. Tasks include budgeting, strategic planning, and personnel decisions for the information systems function. The CIO must also be the face of the IT department within the organization. This involves working with senior leaders in all parts of the organization to ensure good communication, planning, and budgeting.
Interestingly, the CIO position does not necessarily require a lot of technical expertise. While helpful, it is more important for this person to have good management skills and understand the business. Many organizations do not have someone with the title of CIO. Instead, the head of the information systems function is called the Vice President of Information Systems or Director of Information Systems.
Functional Manager
As an information systems organization becomes larger, many of the different functions are grouped together and led by a manager. These functional managers report to the CIO and manage the employees specific to their function. For example, in a large organization there are a group of systems analysts who report to a manager of the systems analysis function. For more insight into how this might look, see the discussion later in the chapter of how information systems are organized.
ERP Management
Organizations using an ERP require one or more individuals to manage these systems. EPR managers make sure that the ERP system is completely up to date, work to implement any changes to the ERP that are needed, and consult with various user departments on needed reports or data extracts.
Project Managers
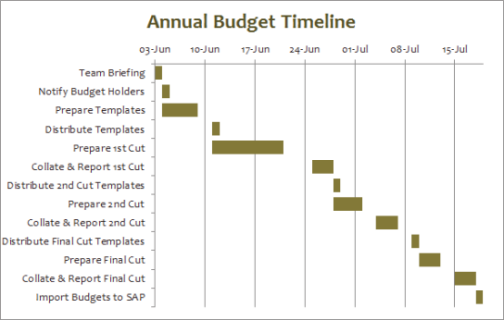
Information systems projects are notorious for going over budget and being delivered late. In many cases a failed IT project can spell doom for a company. A project manager is responsible for keeping projects on time and on budget. This person works with the stakeholders of the project to keep the team organized and communicates the status of the project to management. Gantt charts, shown above, are used to graphically illustrate a project’s schedule, tasks, and resources.
A project manager does not have authority over the project team. Instead, the project manager coordinates schedules and resources in order to maximize the project outcomes. This leader must be a good communicator and an extremely organized person. A project manager should also have good people skills. Many organizations require each of their project managers to become certified as a Project Management Professional (PMP).
Information Security Officer
An information security officer is in charge of setting information security policies for an organization and then overseeing the implementation of those policies. This person may have one or more people reporting to them as part of the information security team. As information has become a critical asset, this position has become highly valued. The information security officer must ensure that the organization’s information remains secure from both internal and external threats.
Emerging Roles
As technology evolves many new roles are becoming more common as other roles diminish. For example, as we enter the age of “big data,” we are seeing the need for more data analysts and business intelligence specialists. Many companies are now hiring social media experts and mobile technology specialists. The increased use of cloud computing and Virtual Machine (VM) technologies also is increasing demand for expertise in those areas.
Career Paths in Information Systems
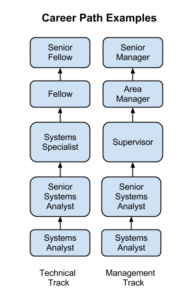
These job descriptions do not represent all possible jobs within an information systems organization. Larger organizations will have more specialized roles, while smaller organizations may combine some of these roles. Many of these roles may exist outside of a traditional information-systems organization, as we will discuss below.
Working with information systems can be a rewarding career choice. Whether you want to be involved in very technical jobs (programmer, database administrator), or you want to be involved in working with people (systems analyst, trainer, project manager), there are many different career paths available.
Many times those in technical jobs who want career advancement find themselves in a dilemma. A person can continue doing technical work, where sometimes their advancement options are limited, or become a manager of other employees and put themselves on a management career track. In many cases those proficient in technical skills are not gifted with managerial skills. Some organizations, especially those that highly value their technically skilled employees, create a technical track that exists in parallel to the management track so that they can retain employees who are contributing to the organization with their technical skills.
Sidebar: Are Certifications Worth Pursuing?
As technology becomes more important to businesses, hiring employees with technical skills is becoming critical. But how can an organization ensure that the person they are hiring has the necessary skills? Many organizations are including technical certifications as a prerequisite for getting hired.
Cisco Certified Internetwork Expert.

Certifications are designations given by a certifying body that someone has a specific level of knowledge in a specific technology. This certifying body is often the vendor of the product itself, though independent certifying organizations, such as CompTIA, also exist. Many of these organizations offer certification tracks, allowing a beginning certificate as a prerequisite to getting more advanced certificates. To get a certificate, you generally attend one or more training classes and then take one or more certification exams. Passing the exams with a certain score will qualify you for a certificate. In most cases, these classes and certificates are not free. In fact a highly technical certification can cost thousands dollars. Some examples of the certifications in highest demand include Microsoft (software certifications), Cisco (networking), and SANS (security).
For many working in IT, determining whether to pursue one or more of these certifications is an important question. For many jobs, such as those involving networking or security, a certificate will be required by the employer as a way to determine which potential employees have a basic level of skill. For those who are already in an IT career, a more advanced certificate may lead to a promotion. For those wondering about the importance of certification, the best solution is to talk to potential employers and those already working in the field to determine the best choice.
Organizing the Information Systems Function
In the early years of computing, the information-systems function (generally called “data processing”) was placed in the finance or accounting department of the organization. As computing became more important, a separate information-systems function was formed, but it still was generally placed under the Chief Financial Officer and considered to be an administrative function of the company. By the 1980s and 1990s, when companies began networking internally and then connecting to the Internet, the information systems function was combined with the telecommunications functions and designated as the Information Technology (IT) department. As the role of information technology continued to increase, its place in the organization became more important. In many organizations today, the head of IT (the CIO) reports directly to the CEO.
Where in the Organization Should IS Be?
Before the advent of the personal computer, the information systems function was centralized within organizations in order to maximize control over computing resources. When the PC began proliferating, many departments within organizations saw it as a chance to gain some computing resources for themselves. Some departments created an internal information systems group, complete with systems analysts, programmers, and even database administrators. These departmental IS groups were dedicated to the information needs of their own departments, providing quicker turnaround and higher levels of service than a centralized IT department. However, having several IS groups within an organization led to a lot of inefficiencies. There were now several people performing the same jobs in different departments. This decentralization also led to company data being stored in several places all over the company.
In some organizations a matrix reporting structure developed in which IT personnel were placed within a department and reported to both the department management and the functional management within IS. The advantages of dedicated IS personnel for each department must be weighed against the need for more control over the strategic information resources of the company.
For many companies, these questions are resolved by the implementation of the ERP system (see discussion of ERP in Chapter 8). Because an ERP system consolidates most corporate data back into a single database, the implementation of an ERP system requires organizations to find “silos” of data so that they can integrate them back into the corporate system. The ERP allows organizations to regain control of their information and influences organizational decisions throughout the company.
Outsourcing
Frequently an organization needs a specific skill for a limited period of time. Instead of training existing employees or hiring new staff, it may make more sense to outsource the job. Outsourcing can be used in many different situations within the information systems function, such as the design and creation of a new website or the upgrade of an ERP system. Some organizations see outsourcing as a cost-cutting move, contracting out a whole group or department.
New Models of Organizations
The integration of information technology has influenced the structure of organizations. The increased ability to communicate and share information has led to a “flattening” of the organizational structure due to the removal of one or more layers of management.
The network-based organizational structure is another changed enabled by information systems. In a network-based organizational structure, groups of employees can work somewhat independently to accomplish a project. People with the right skills are brought together for a project and then released to work on other projects when that project is over. These groups are somewhat informal and allow for all members of the group to maximize their effectiveness.
Information Systems Users – Types of Users
Besides the people who work to create, administer, and manage information systems, there is one more extremely important group of people, namely, the users of information systems. This group represents a very large percentage of an organization’s employees. If the user is not able to successfully learn and use an information system, the system is doomed to failure.
Technology adoption user types
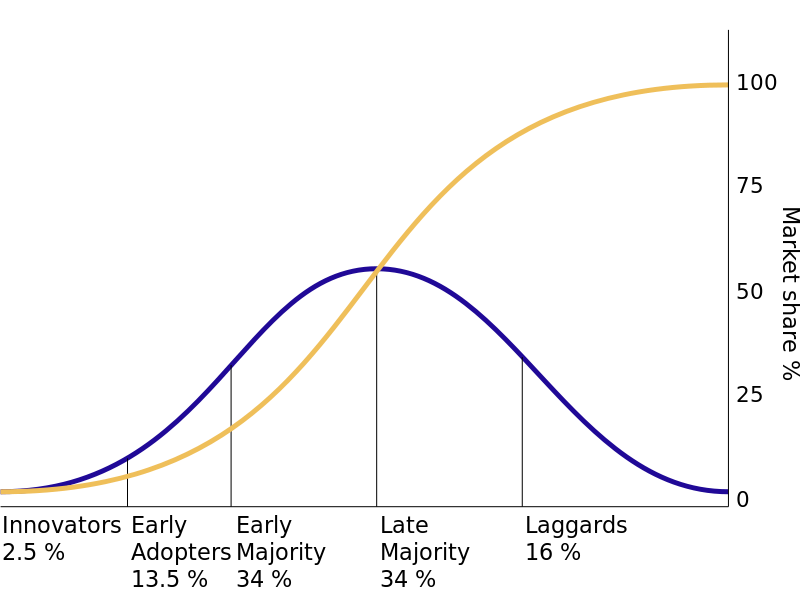
One tool that can be used to understand how users will adopt a new technology comes from a 1962 study by Everett Rogers. In his book, Diffusion of Innovation,[1]Rogers studied how farmers adopted new technologies and noticed that the adoption rate started slowly and then dramatically increased once adoption hit a certain point. He identified five specific types of technology adopters:
- Innovators. Innovators are the first individuals to adopt a new technology. Innovators are willing to take risks, are the youngest in age, have the highest social class, have great financial liquidity, are very social, and have the closest contact with scientific sources and interaction with other innovators. Risk tolerance is high so there is a willingness to adopt technologies thast may ultimately fail. Financial resources help absorb these failures (Rogers, 1962, p. 282).
- Early adopters. The early adopters are those who adopt innovation soon after a technology has been introduced and proven. These individuals have the highest degree of opinion leadership among the other adopter categories, which means that these adopters can influence the opinions of the largest majority. Characteristics include being younger in age, having a higher social status, possessing more financial liquidity, having advanced education, and being more socially aware than later adopters. These adopters are more discrete in adoption choices than innovators, and realize judicious choice of adoption will help them maintain a central communication position (Rogers, 1962, p. 283).
- Early majority. Individuals in this category adopt an innovation after a varying degree of time. This time of adoption is significantly longer than the innovators and early adopters. This group tends to be slower in the adoption process, has above average social status, has contact with early adopters, and seldom holds positions of opinion leadership in a system (Rogers, 1962, p. 283).
- Late majority. The late majority will adopt an innovation after the average member of the society. These individuals approach an innovation with a high degree of skepticism, have below average social status, very little financial liquidity, are in contact with others in the late majority and the early majority, and show very little opinion leadership.
- Laggards. Individuals in this category are the last to adopt an innovation. Unlike those in the previous categories, individuals in this category show no opinion leadership. These individuals typically have an aversion to change agents and tend to be advanced in age. Laggards typically tend to be focused on “traditions,” are likely to have the lowest social status and the lowest financial liquidity, be oldest of all other adopters, and be in contact with only family and close friends.[2]
These five types of users can be translated into information technology adopters as well, and provide additional insight into how to implement new information systems within the organization. For example, when rolling out a new system, IT may want to identify the innovators and early adopters within the organization and work with them first, then leverage their adoption to drive the rest of the implementation to the other users.
Summary
In this chapter we have reviewed the many different categories of individuals who make up the people component of information systems. The world of information technology is changing so fast that new roles are being created all the time and roles that existed for decades are being phased out. This chapter this chapter should have given you a good idea and appreciation for the importance of the people component of information systems.
Study Questions
- Describe the role of a systems analyst.
- What are some of the different roles for a computer engineer?
- What are the duties of a computer operator?
- What does the CIO do?
- Describe the job of a project manager.
- Explain the point of having two different career paths in information systems.
- What are the advantages and disadvantages of centralizing the IT function?
- What impact has information technology had on the way companies are organized?
- What are the five types of information-systems users?
- Why would an organization outsource?
Exercises
- Which IT job would you like to have? Do some original research and write a two-page paper describing the duties of the job you are interested in.
- Spend a few minutes on Dice or Monster to find IT jobs in your area. What IT jobs are currently available? Write up a two-page paper describing three jobs, their starting salary (if listed), and the skills and education needed for the job.
- How is the IT function organized in your school or place of employment? Create an organization chart showing how the IT organization fits into your overall organization. Comment on how centralized or decentralized the IT function is.
- What type of IT user are you? Take a look at the five types of technology adopters and then write a one-page summary of where you think you fit in this model.
Lab
- Define each job in the list, then ask 10 friends to identify which jobs they have heard about or know something about. Tabulate your results.
- Chief marketing technologist
- Developer evangelist
- Ethical hacker
- Business intelligence analyst
- Digital marketing manager
- Growth hacker
- UX designer
- Cloud architect
- Data detective
- Master of edge computing
- Digital prophet
- NOC specialist
- SEO/SEM specialist
